What is a dusting attack?
A crypto dusting attack is a distribution of small amounts of cryptocurrency to numerous cryptocurrency wallets. This activity is undertaken with the intention of flushing out the identity of a wallet owner.
In this article, we’ll look at how crypto dusting attacks work and how to protect against them, using Bitcoin as an example.
What is Bitcoin dust?
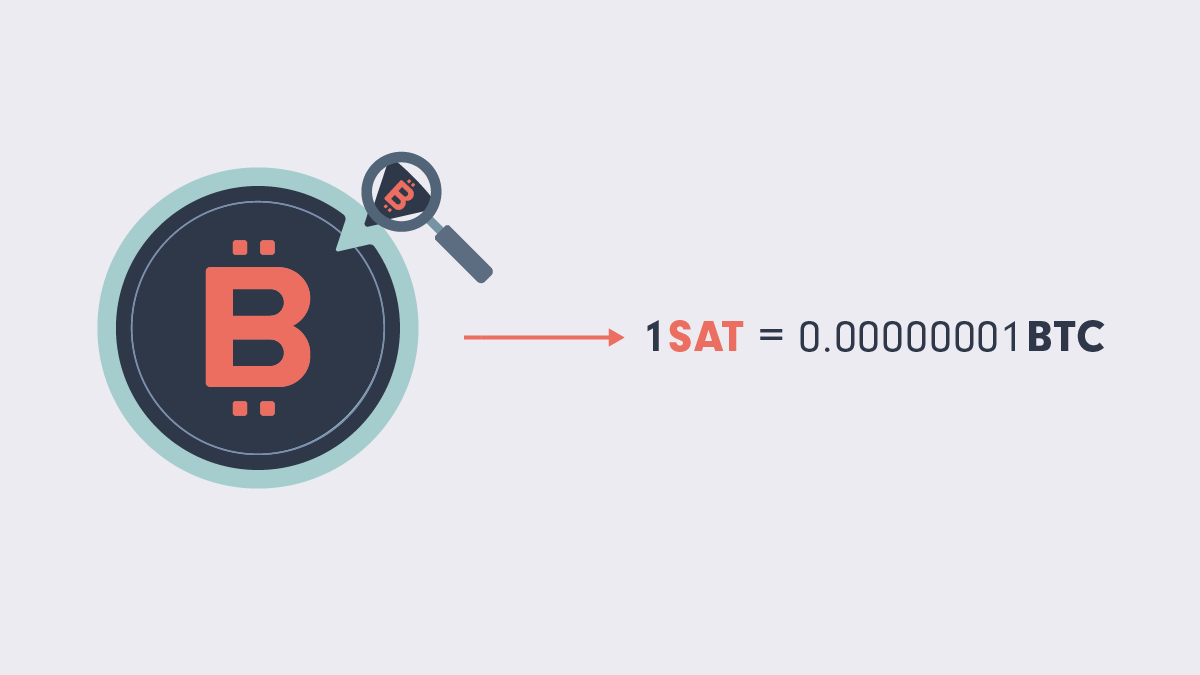
Bitcoin’s smallest denomination is one satoshi (sat). One sat is one 100-millionth of one BTC. At the time of writing, $1 is worth about 2,000 sats.
Bitcoin dust is simply a very small amount of BTC, often defined as no more than several hundred sats, equivalent to just a few cents.
Units of Bitcoin are recorded in UTXOs, or unspent transaction outputs. The key thing to know is that UTXOs are irregular and indivisible amounts of Bitcoin.
For example, if you have a UTXO worth 3 BTC and wish to send someone else 1 BTC, the only way to do that is to create a new transaction to “spend” the original 3 BTC UTXO. This transaction returns the “change” to you in the form of a new UTXO worth 2 BTC.
If you send or receive a number of transactions using small UTXOs, you may end up with a natural accumulation of dust in your wallet.
See also: What is UTXO management?
How does a Bitcoin dusting attack work?
A dusting attack involves sending small amounts of Bitcoin to many addresses, with the purpose of gathering information about the recipients.
Crypto dusting can be for nefarious purposes, or it can be for research purposes.
When used for nefarious activity, a dusting attack can arm a criminal with enough information to attempt a scam such as a phishing attack.
In the worst-case scenario, it can reveal the identity of a crypto whale — an individual or organization that holds vast amounts of cryptocurrency.
Once a criminal knows the identity of a whale, they can make an ultimatum and demand a ransom to avoid it. This ultimatum could be a physical threat such as bodily harm or kidnapping. It could also be a digital threat such as holding files or information for a ransom.
What happens in a dusting attack?
When a Bitcoin address receives a dust deposit, the transaction is recorded on the blockchain.
If the recipient then combines the dust UTXOs with other UTXOs that they own in order to create a transaction, they will be connected on the blockchain.
The sender of the dust can then connect the dots between the public wallet addresses of the dust UTXOs and other UTXOs that the recipient owns and sends or receives.
By analyzing the wallet’s transaction patterns, they might even be able to piece together the identity of the wallet holder.
How to protect against dusting attacks
We cannot prevent dust being sent to us, because anyone can send Bitcoin to a wallet address that is public on the blockchain. This means any address that has previously been involved in a transaction.
What we can do is protect our anonymity by not spending the dust.
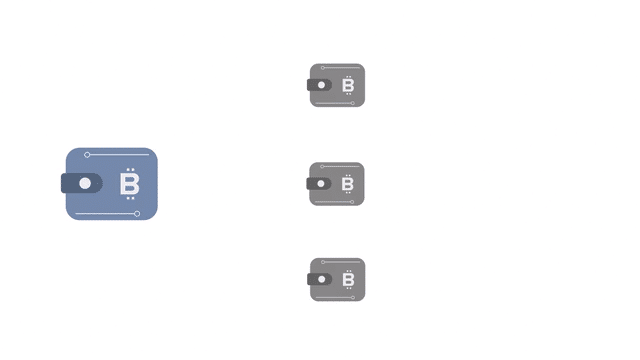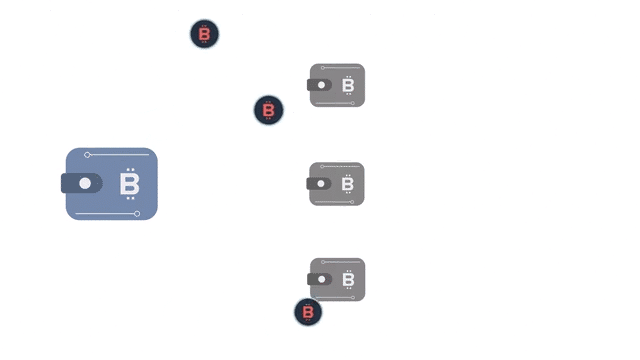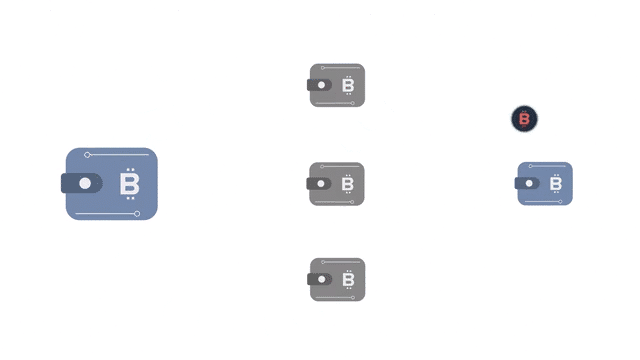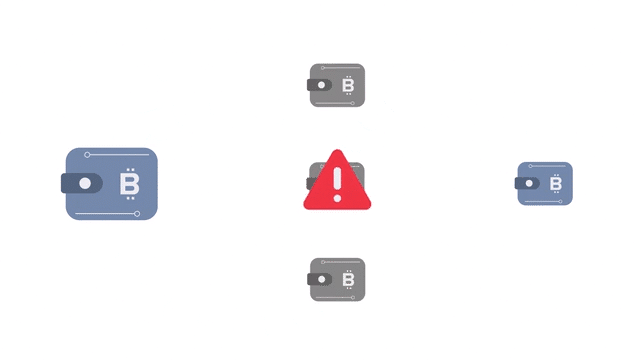
Protection against dust attacks for enterprise business
Things get more complicated for large corporations using Bitcoin in their business operations.
Enterprise-level users often make large numbers of transactions using multiple wallets. The organization might not care about maintaining the anonymity of its public-facing wallet and thus might choose to spend unsolicited dust.
However, this dust should never be transferred from an organization’s public-facing wallet to a wallet intended for internal use only.
That’s because of the business-sensitive information that might be revealed.
If internal wallets are used to transfer funds between different parts of the business, for example, then analysis of transaction patterns could give attackers an idea of the organization’s total BTC balance.
So as we have seen, maintaining control over which UTXOs are used in a transaction is key for protecting against dusting attacks. This is why good UTXO management is particularly important for enterprise business.
Further reading: How to deflect a Bitcoin dusting attack in three steps.
Fortris handles digital asset treasury operations for enterprise business.
Want to learn more? Book a demo today.
